Skills Knowledge Enhancement - Main
The course outline and timetable can be seen here. The timetable is subject to alteration dependent upon the needs of the group.
If you are a new student enrolled on the Staffordshire University SKE course please register, once and once only, using the Student Registration Form. To view the student registration list, the username is the name of the school which made front page of their local paper and the password is how I describe the Headteacher who presided over the scandal (no spaces).
There are some great resources for teaching Computer Science that have come out of New Zealand in recent years: Computer Science Unplugged and The Computer Science Field Guide. The Computer Science Field Guide is an online resource for teaching Computer Science to students. This guide was initially developed as an online interactive textbook to support the new achievement standards in Computer Science that were being rolled out in New Zealand (2011-2013), and is now being adapted for use all over the world. Computer Science Unplugged is a wonderful set of resources and ideas for use in the classroom. Although it was developed for primary school students, many of the areas covered are relevant to computer science topics up to GCSE level. There is also a booklet to accompany the resources that adds further explanation.
Examples of previous portfolios: SKE student 1 SKE student 2. If you're not confident it setting up a web style portfolio from scratch, why not modify a free template. If you're completely new to HTML, or you are looking for a resource to teach HTML and CSS to other's, have a look at HTMLdog.
If your portfolio is in a web site format here is a useful tool for tidying the HTML.
Geek Gurl has produced 41 short videos that explains what Computer Science is. See them all or pick out particular topics.
Back to Top
Hardware, peripherals and Software
A computer system is made up of hardware, peripherals and software and is able to take in data (input), process data (process) and output results (output). Computer systems are not just computers, as we know them, but the definition also applies to any equipment that uses computer technology. That is, technology that has a a computer 'embedded' in that system. Eg Smart TV, Mobile Phone, cameras, etc.
Hardware is the collective term to describe all the physical components of a computer system. Hardware devices that are external to the main body of a computer are called Peripherals. A list and description of commonly used hardware can be found at gcsecomputing.org.uk/. A comprehensive list of hardware, with definitions, can be be found on the Computer Hope site.
Software describes the programs and data that is needed to make the hardware work.
Task: Take a PC apart and see if you can identify all the component parts and explain the function of each component.
Back to Top
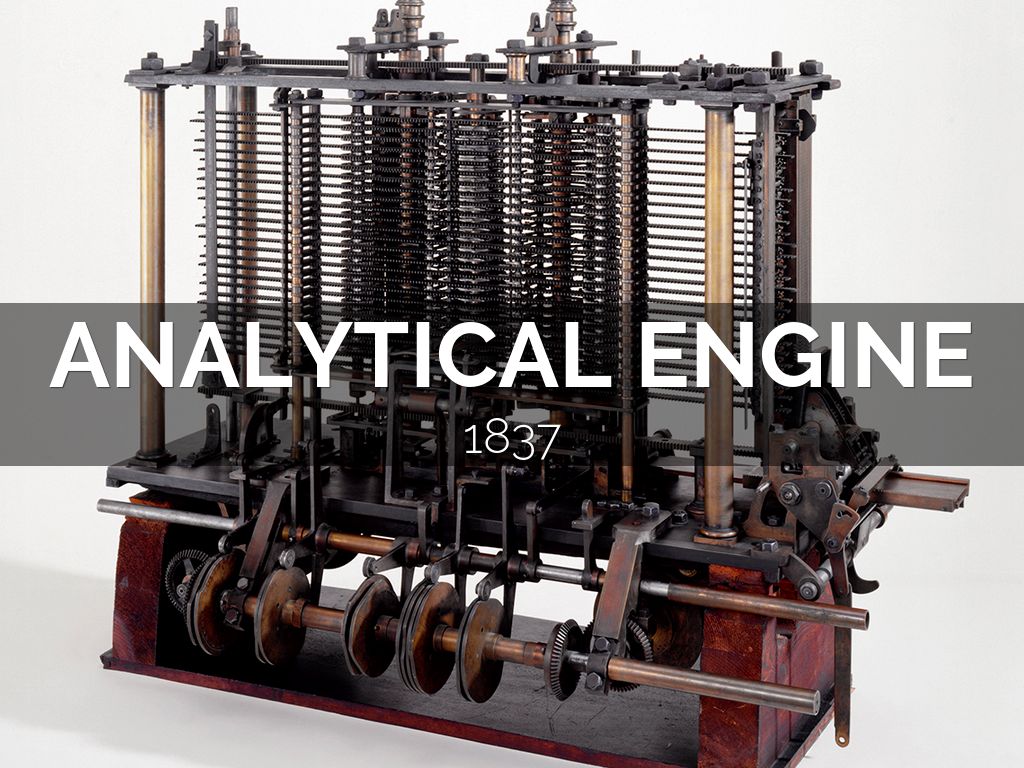
The basic model of a modern digital computer hasn't changed much since Charles Babbage propsoesd his Analytic Engine around 1830. His design consisted of a Mill (today we would know it as the ALU), the Store (today, memory), the Operator (today, the Control Unit) and Output (today, I/O devices).
Central Processing Unit (CPU)
Today the central processing unit (CPU) is the electronic circuitry within a computer that carries out the instructions of a computer program by performing the basic arithmetic, logical, control and input/output (I/O) operations specified by the instructions. Every CPU has its own unique instruction set or machine language.
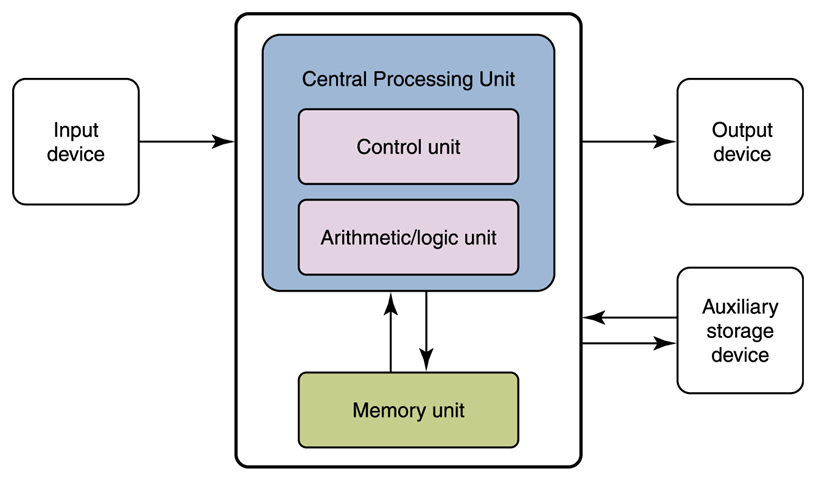 The mathematician, John von Neumann, proposed storing instructions in the memory of a computer and using a control unit to handle
the fetch-decode-execute cycle (fetch the instruction, decode the instruction, execute the instruction).
The mathematician, John von Neumann, proposed storing instructions in the memory of a computer and using a control unit to handle
the fetch-decode-execute cycle (fetch the instruction, decode the instruction, execute the instruction).
There are 3 major units in a computer tied together by buses:
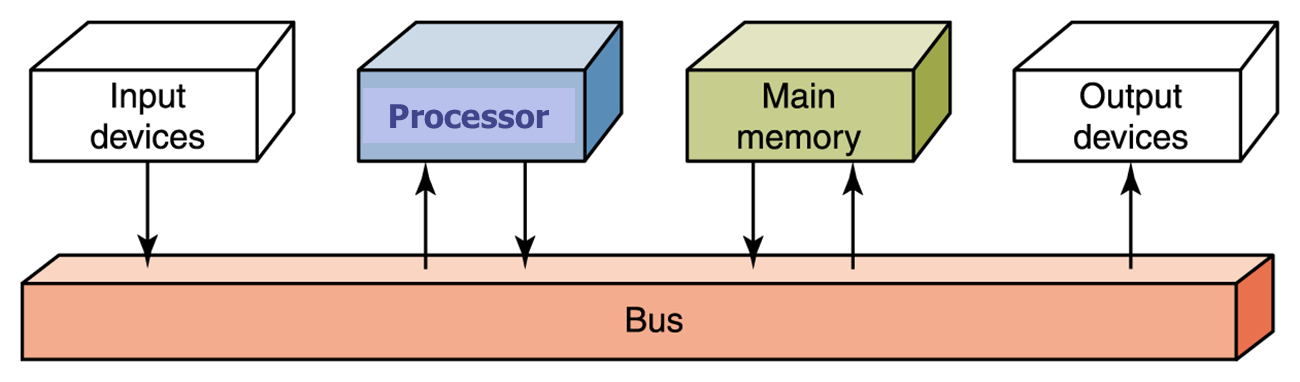
1) Memory - The unit that stores and retrieves instructions and data.
2) Processor: The unit that houses two separate components; the control unit and the ALU.
3) Input/Output (I/O) Units - Handles communication with the
outside world.
A much more detailed explanation of Computer Architecture, based on the von Neumann model, can be found in a presentation based on one put together by J Baker at Kent State University.
The Instruction Cycle on Wikipedia is also worth investigating. You need to understand the various CPU components:
- Program Counter (PC) - An incrementing counter that keeps track of the memory address of the instruction that is to be executed next or in other words, holds the address of the instruction to be executed next.
- Memory Address Register (MAR) - Holds the address of a block of memory for reading from or writing to.
- Memory Data Register (MDR) - A two-way register that holds data fetched from memory (and ready for the CPU to process) or data waiting to be stored in memory. (This is also known as the memory buffer register(MBR).)
- Instruction Register (IR) - A temporary holding ground for the instruction that has just been fetched from memory.
- Control Unit (CU) - Decodes the program instruction in the IR, selecting machine resources, such as a data source register and a particular arithmetic operation, and coordinates activation of those resources.
- Arithmetic Logic Unit (ALU) - Performs mathematical and logical operations
In a computer or on a network, a bus is a transmission path on which signals are dropped off or picked up at every device attached to the line. Only devices addressed by the signals pay attention to them; the others discard the signals. The name probably comes from the similarity to buses following a set route, picking up and dropping off passengers at the correct destination.
CPU Cache memory, also called CPU memory, is random access memory (RAM) that a computer microprocessor can access more quickly than it can access regular RAM. This memory is typically integrated directly with the CPU chip or placed on a separate chip that has a separate businterconnect with the CPU.
Geek Gurl has produced rapid run-throughs of the ALU, Registers and RAM and the CPU. Well worth a look!
Machine language
This is the lowest-level programming language. Machine languages are the only languages understood by computers. While easily understood by computers, machine languages are almost impossible for humans to use because they consist entirely of numbers. Programmers, therefore, use either a high-level programming language or an assembly language. An assembly language contains the same instructions as a machine language, but the instructions and variables have names instead of being just numbers.
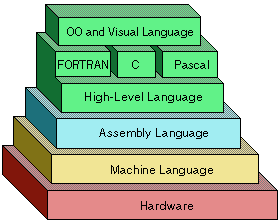
Assembly language programs are translated into machine language by a program called an assembler.
Every CPU has its own unique machine language or instruction set. Programs must, therefore, be rewritten or recompiled to run on different types of computers.
A digital is computer made of thousands and thousands of switches that can be in only two states, a on or off (0 or 1), and we therefore use a number system that only has 2 digits to represent what is happening inside it. This number system is called Binary and only the digits 0 and 1 are allowed in this number system.
If you want to write some programs in a low-level language, try the 'Assembler and Little Man Computer', in the Coding section of the site.
Back to Top
Humans count using a number system based on tens, probably because we have ten digits, but because computers are two state devices, it prefers a number system based on two digits, the BINARY number system. Test yourself.
Have a look at Geek Gurl's take on Binary.
Whilst binary is the preferred language of the computer, it is not very convenient for humans to think and work in binary. Hexadecimal equivalents of binary are much shorter in length and therefore easier for humans to work with, whilst also being acceptable for a computer to use because hex can be quickly translated into binary.
Eg. The colour Magenta in Hexadecimal (Base 16) is 5AA1C4
but the same colour in binary is 010110101010000111000100
The ancient Martians in 'Total Recall' had 4 digits on their hands. I suspect that they used a number system based on 8 digits, OCTAL. Test your Octal.

I haven't met, or been abducted by, any 16 fingered aliens but the number system based on 16 is called HEXADECIMAL. Test yourself on Binary, Octal and Hex.
Useful resources:
Cisco Binary 'Tetris' game Uses Java and so must be run through Internet Explorer. It will not run through Chrome or Edge. You may also need to get a Cisco Logon.
John Philip Jones has produced an excellent series of FREE videos that cover many GCSE Computer Science topics. Have a look at his binary video. Find the spy using binary skills.
a spreadsheet showing decimal, binary, hexadecimal and ASCII, and Representing data and if you want to create your own worksheets, try worksheetworks.com.
Adding binary numbers is the currently the only mathematical operation that is needed for GCSE. It's not as difficult as you may think!
Starter exercise: Binary Bingo
Back to Top
Scientific Notation
When we have to write very large or very small numbers, it is easier to write them in scientific notation.
Eg.
351,000,000,000 = 3.51 x 1011
(sign is positive, 3.51 is Mantissa, 11 is the Exponent and 10 is the number base)
and
0.00000000124 = 1.24 x 10-9
(sign is positive, 1.24 is Mantissa, -9 is the Exponent and 10 is the number base)
Notice that we place the decimal point just to the right of the leftmost nonzero digit in the value. We call the leftmost nonzero digit the most significant digit. In the text the decimal point is placed to the left of the most significant digit, but we shall always put the decimal point to its right.
Floating Point Number
On a computer, a real number is often called a floating point number. Floating point numbers are stored in a fixed number of bits of computer memory. The exact number of bits depends on the computer system being used.
The IEEE 754 32-bit standard uses 1 bit for the sign of the number, 23 bits for the fractional part (mantissa) and 8 bits for the exponent.
![]()
Sign Exponent Mantissa
To allow for negative exponents a bias of 127 is used.
Eg1
Represent 13.1875 in floating point binary.
As it is positive, the sign bit is 0
1310 = 11012
0.187510 = .00112
Therefore, 13.187510 = 1101.00112
= 1.10100112 x 23
The 1 before the binary point is not stored because this will always be a 1. The 23-bit mantissa is, therefore, 10100110000000000000000
The exponent of 3 has a bias of 127 applied to it and it is then converted to binary to give the exponent.
3 + 127 = 130
13010 = 100000102
The exponent is 10000010
13.187510 is represented by 0 10000010 10100110000000000000000
A video which demonstrates this example can be found on YouTube and a website to convert from denary into floating binary representation is also available.
Back to Top
Utility software is system software designed to help analyse, configure, optimise or maintain a computer. It is used to support the computer infrastructure in contrast to application software, which is
aimed at directly performing tasks that benefit users.
Although a basic set of utility programs is usually distributed with an operating system (OS), utility software is not considered part of the OS and users
often install replacements or additional utilities such as software for encryption, defragmentation, data compression (see below), backing up (full or incremental).
Encryption
If you want to send digital information securely you have to be careful. Any message sent over a network can be intercepted. Encryption is a method of changing the original numbers and characters so that they are hidden or disguised. This is important if you are sending sensitive information.
The prefix for some web addresses is https instead of http. The ‘s’ indicates that it is a secure website and any payment or personal details that are inputted into the site will be encrypted.
What is defragmentation and why do I need it?
Defragmentation is like cleaning house for your PC, it picks up all of the pieces of data that are spread across your hard drive and puts them back together again. Why is defragmentation important? Because every computer suffers from the constant growth of fragmentation and if you don’t clean house, your PC suffers.
Disk fragmentation occurs when a file is broken up into pieces to fit on the disk. Because files are constantly being written, deleted and resized, fragmentation is a natural occurrence. When a file is spread out over several locations, it takes longer to read and write. But the effects of fragmentation are far more widespread: Slow PC performance, long boot-times, random crashes and freeze-ups – even a complete inability to boot up at all. Many users blame these problems on the operating system or simply think their computer is “old”, when hard disk fragmentation is most often the real culprit.
Backing Up
A Full Backup captures your entire system and all the data you want to protect. Frequent full backups result in easier recovery operations.
Pros: Fast, reliable recovery
Cons: Slower backup, lots of storage required
An Incremental Backup captures only the changes made since the last incremental backup. When compare to a Full Backup this saves both time and storage space and ensures that your backup is up to date.
Pros: Fast backups, low storage space
Cons: Slower recovery, risk of data loss
Back to Top
Remind yourself of what a database is by completing the definitions on this Database Worksheet and create the Student Mobile Phone database mentioned in the Database Worksheet.
Compare your definitions with your neighbour so that you have an agreed set of identical definitions. Compare your definitions with another pair's definitions and again agree on a group set of definitions.
The worksheet also points you towards SQL tutorials on w3schools.com
A Power Point presentation and an accompanying database was produced by two previous SKE students. Give it a try.
Now write some SQL statements for the Student Mobile Phone database.
Make notes on the meaning of the following SQL statements:
- SELECT, FROM, WHERE, LIKE, AND, OR
- and also explain the wildcards * and %
Back to Top
Solutions to simple problems could be designed and implemented just by sitting at a computer and writing code. Solutions to complex problems, however, need to be planned.
Flowcharts and Pseudocode are common methods used to describe algorithms. Both use structural conventions of programming languages and allow the coder to concentrate on the algorithm rather than the nuances and details of a programming language. These methods, although written with the intentention of coding the solution in a high level language later, they should be independent of any particular language. Both tools are a useful step in achieving well written code.
Flowcharts use shapes to represent different actions that you want your program to perform in order to arrive at a solution to a problem.
Pseudocode is an informal high-level description of the operating principle of a computer program or other algorithm. It is intended for human reading rather than machine reading.
Flowcharting
Flowgorithm, Gliffy, Creately, Word and Excel are all 'free' flowcharting tools but I expect that there any others.
I would suggest that you investigate the merits of all of these tools but Flowgorithm is particularly cool because you can create a flowchart, execute it directly in Flowgorithm AND convert the flowchart to Pseudocode or many popular languages! These include: C#, C++, Delphi/Pascal, Java, JavaScript, Lua, Perl, Python, QBasic, Ruby, Swift 2, Visual Basic .NET, and Visual Basic for Applications (used in Office)! Having downloaded and installed Flowgorithm, follow the quick tutorial.
Here's a solution to Python Exercises number 7and here is a web page which illustrates the difference between If...Then and Elseif both in code and flowcharting. The site also contains illustrations of other flow control statements.
A book that does exactly what it says in the title, which is written in easily digestible chapters, is 'Problem Solving with Flowcharts and a Little Flavor of Programming with Python' (By Achla Agarwal, Krishna Agarwal, Laura Goadrich, and Mark Goadrich - ISBN 9780557276349. Also available as a pdf download from lulu.com)
The book is written for students of any age who want to learn the concepts to enable them to program successfully. Programming is an art and this text will teach you the techniques and underlying logic that will form the foundation of future coding skills, no matter what language you choose to program in. Because there are a variety of programming languages that are changing and evolving, it is important to create a solid skill-set that is adaptable to any programming language you choose to learn.
Accompanying the book are a number of very simple, self-marking, quizzes:
- Chapter 1 - Techniques for Problem Solving quiz
- Chapter 2 - Storing Data quiz
- Chapter 3 - Pseudocode, Flowcharts and Python quiz
- Chapter 4 - Input and Output quiz
- Chapter 5 - Boolean Variables quiz
- Chapter 6 - Selection Structures quiz
- Chapter 7 - Nested If-Then-Else and Case Statements quiz
- Chapter 8 - Repetition Structures quiz
OCR Programming assignment - Teacher Quiz
Flowchart solutions to the tasks are Task 1, Task 2 and Task 3T
Pseudocode & Lynda
A short video explaining pseudocode, with examples, can be seen on Youtube. It has been 'ripped off' from Lynda.com. Lynda is a fabulous resource that you have access to using your Staffs University login that has many training videos, covering a wide range of subjects, not only computer related courses but also such things as CAD, Marketing, Audio/Music and many more.
Some more examples of pseudocode, unrelated to the above book, are here. The Pearson Specification (pp 41- 47) has a suggested 'Pseudocode Command Set
Practise writing code from Pseudocode
Here are pseudocode solutions to some simple problems - Pseudocode solutions.
| Translate the pseudocode into code in Python |
| Adopt your own pseudocode style and re-write them in your style |
| Turn the examples in Edexcel's An Introduction to Python into pseudocode |
Back to Top
A trace table is a technique used to test algorithms, in order to make sure that no logical errors occur whilst the algorithm is being processed. The table usually takes the form of a multi-column, multi-row table; with each column showing a variable, and each row showing each number input into the algorithm and the subsequent values of the variables. Eg. Months of the year.
Trace tables are typically used in schools and colleges when teaching students how to program. They can be an essential tool in teaching students how a certain algorithm works and the systematic process that is occurring when the algorithm is executed. They can also be useful for debugging applications, helping the programmer to easily detect what error is occurring, and why it may be occurring
Using the flowchart and pseudocode for Pay with Overtime, write a solution in Python and create 3 Trace Tables to verify the solution using a rate of £7.38 and hour and times of 29, 40 and 43 hours.
Using the flowchart Average of 4 numbers, write a solution in Python. Create a Trace Table to verify that the solution works using 7, 4 16 and 32.
Create a Trace Table for the cm to inch conversion program in the Python Exercises.
Back to Top
CAS have produced some summary documents that help to explain the government's 2014 Computing National Curriculum. There is a Primary overview, a Secondary one and a Progression Pathway which indicates the development path that a student should follow to achieve 'computing enlightenment' (Grasshopper!)
Other CAS explanatory documents that may be useful: Developing Computational Thinking, Computational Thinking - A guide for teachers, Progression Pathways WITH Badges and Progression Pathways WITHOUT Badges. The Department for Education statutory guidance may also be worth a look.
In pairs, produce a 15 minute presentation that explains nature of the Computing National Curriculum and the challenges that schools face.
Back to Top
A course of tutorials is available for Flowol 4.
Back to Top
Common craft style videos are crudely produced, short, films that can be used to describe how something works. Here's an example of a specification for small group work to produce a Common Craft style video about Secondary Storage. Some useful notes on how to create a Common Craft Style Video are here.
An alternative to Common Craft is a poster. Here's an example showing the inside of a hard drive, courtesy of ebuyer.com.
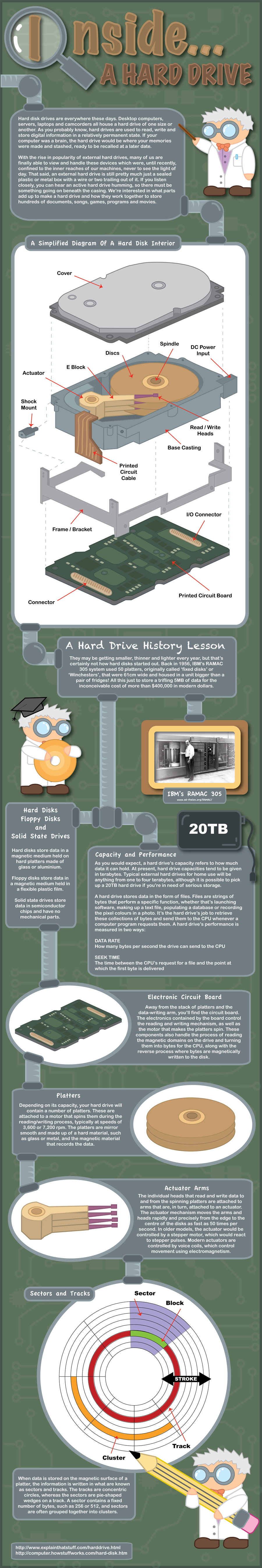
Back to Top
John Philip Jones has produced some super videos on many aspects of Computer Science. Here's one that takes Logic from the beginning. Richard Herbert has produced a PowerPoint presentation that could also serve as a useful introduction to the topic.
A Logic Gate simulator that has limited functionality but is adequate for our needs, can be found at http://logic.ly/demo/. Currently the only gates that need to be considered for GSCE are AND, OR, and NOT. There are exercises that will lead you from Truth Tables for individual logic gates to Truth Tables for cominations of these gates.
Boolean Notation allows us to write Boolean expressions to describe logic circuits. A list of the common logic functions and their equivalent Boolean notation, along with the questions below, can be downloaded here.
Can you find the Boolean algebra expression for the following systems?
1.
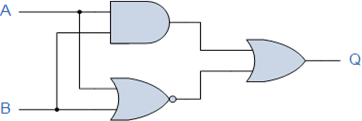
2.
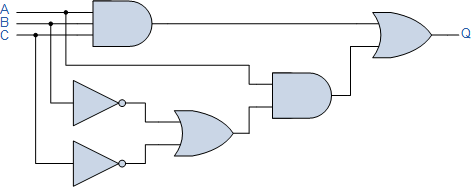
Can you draw the circuit diagram to implement these expressions?
3.
![]()
4.
![]()
Useful tips. This expression was created in Word by a) Insert , b)Equation, c) Accent, d) Overbar
To get XOR symbol, type 2295 then press Alt/X
This extract from Cambridge IGCSE Computer Science Revision Guide may help with your understanding of Logic and may also be a very useful resource for your classroom! Here's a worksheet that might also be a useful resource but it does contain gates that are outside the current scope of GCSE specifications.
Back to Top
CAS have made available an excellent tool for demonstrating bitmapped image manipulation. A video explaining the possibilities is available on Youtube and the tool needed to convert an image into a csv file of RGB values can be downloaded here.
A useful skill in Excel is to copy a cell into all cells in a column. Highlight the cell, select copy, hold down the Shift and Ctrl keys and then press the Up Arrow key.
Resources: BitmapActivity and worksheet to accompany the spreadsheet.
Produce the outline of a lesson plan that uses some of the ideas from this section.
Back to Top
Compression means to reduce the size of a data file. For example a document, spreadsheet, image, sound file etc.
It is a good idea to compress large files because they can take up a lot of storage space on your hard disk. They will also take a long time to send as an attachment by email.
Before you can use a compressed file, you must uncompress it.
There are two types of compression: lossy and lossless. Lossy compression means removing data to reduce the file size. But lossless compression shrinks the whole file, keeping all of the quality. With lossless compression, files can be restored back to their original state. With lossy compression, once you’ve removed the data, it’s gone for good.
Compression is usually carried out by using a piece of utility software such as 'WinZip'.
CS Unplugged has some good exercises that illustrate how data compression works.
Back to Top
ISBN numbers are created so that the first twelve digits are information digits and the last digit, the one you want to calculate, is a check digit. This last number helps people notice and correct mistakes that might be made in recording the information digits. The algorithm for calculating the check digit for an 13-digit International Standard Book Number (ISBN) is best demonstrated by example. Enter a valid ISBN into this spreadsheet.
Back to Top
Software life cycle models describe phases of the software cycle and
the order in which those phases are executed. There are lots of
models, and many companies adopt their own, but all have very similar
patterns.
There are various Software development models or methodologies. They are as follows:
Back to Top
Just as any other specialised subject, there are terms and acronyms that are not in common use outside of that subject. Computer Science is no different and by now you should have quite a useful list of terms. There are many glossaries available on the internet but here is a good one to start with, that should be a useful addition to your own.
A comprehensive list of hardware, with definitions, can be be found on the Computer Hope site.
Back to Top
Coding Challenges (with some solutions)
Pythonschool.net solutions (github)
UsingPython.com solutions master password is 'sellotape'
Back to Top
